These targeted malicious code. Viruses can range in severity from simple programs that display a message or graphic as a joke to more malevolent code that will destroy files or reformat the.
Identify at least three 3 different types of viruses and describe the main differences between each one.
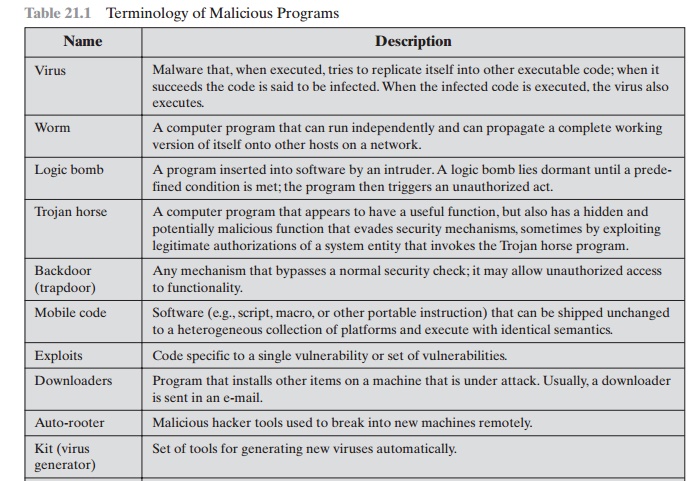
. Next explain both the potential threat posed by viruses and other malicious codes and their main effects on. TABLE 3-1 Types of Malicious Code. A virus is a form of malware that is capable of copying itself and spreading to other computers.
Possibly the most common type of malware viruses attach their malicious code to clean code and wait for an unsuspecting user or an automated process to execute them. 1From the first e-Activity explain the key differences between viruses and other malicious codes. Explain the key differences between viruses and other malicious codes.
Furthermore two or more forms of malicious code can be combined to produce a third kind of problem. Identify at least three different types of viruses and describe the main differences between each one. A virus is a computer program that can replicate or make copies of itself and spread to other files.
It often manifests itself as a browser pop-up and may or may not be malicious in nature. A common type of malicious code is the virus which is a little program attaching to other programs or files and will copy itself in a computer and even spread to other networked computers. Cyber crimes are categorized into three broad categories individual property and government.
Viruses can range from being relatively harmless to causing significant damage to a system. Viruses often spread to other computers by attaching themselves to various programs and executing code when a user launches one of those infected programs. Discuss the motivations of an attacker and the purpose of attacks and briefly explain types of attacks.
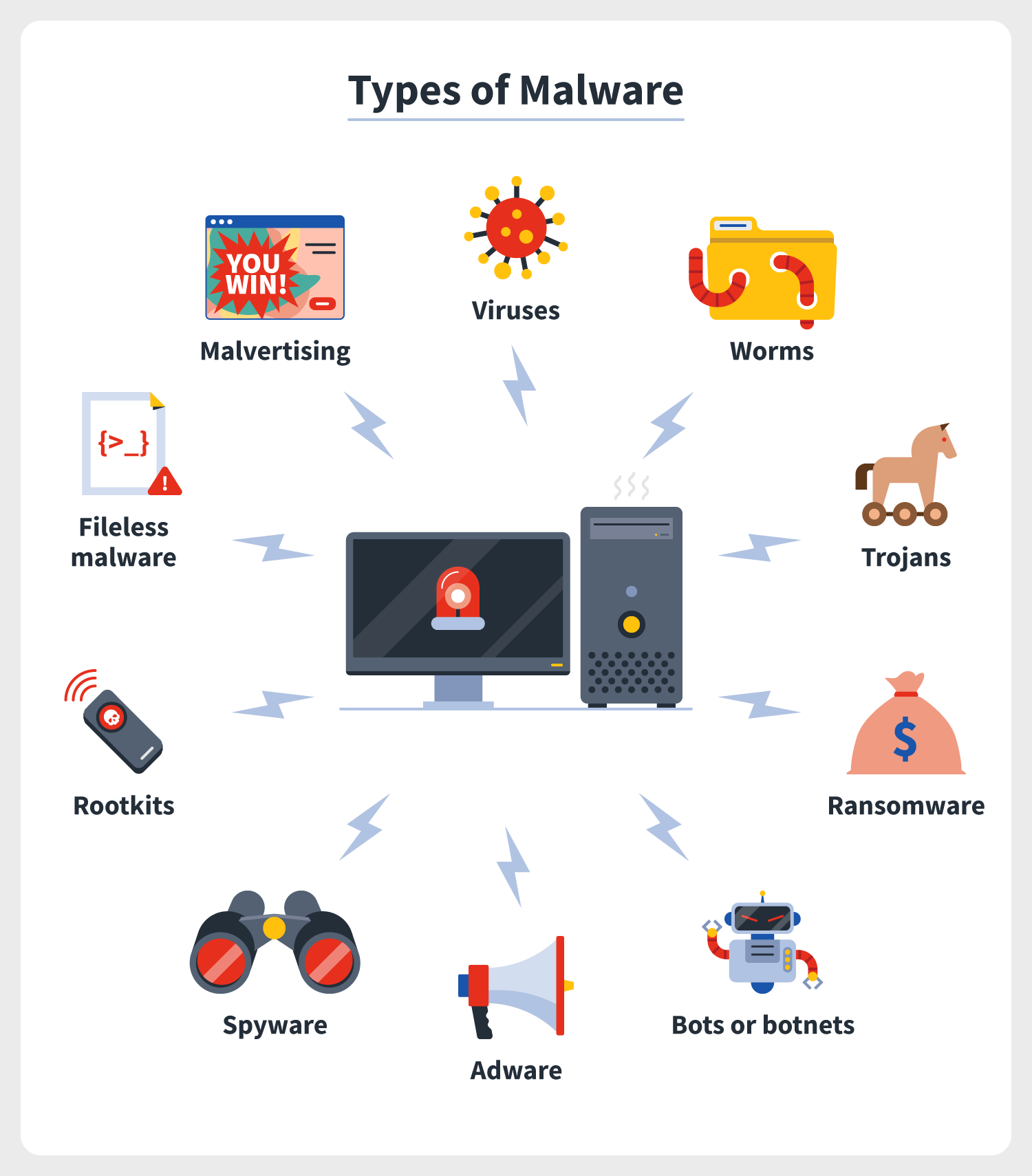
Malicious code may also include time bombs hardcoded cryptographic constants and credentials deliberate information and data leakage rootkits and anti-debugging techniques. A computer worm is a kind of malicious program that replicates itself to spread to as many devices as. Malicious code describes a broad category of system security terms that includes attack scripts viruses worms Trojan horses backdoors and malicious active content.
As viruses worms Trojan horses ransomware and bot programs. Software that automatically downloads or displays unsolicited advertisements. Based on each category of cyber crime cybercriminals use different levels and types of threats.
Week 5 Discussion Virus and Malicious Code Please respond to the following. The types of malicious code are. A computer virus is a type of malicious application that executes and replicates itself by.
The kinds of malicious code are summarized in Table 3-1. For instance a virus can be a time bomb if the viral code that is spreading will trigger an event after a period of time has passed. Malicious code examples include backdoor attacks scripting attacks worms trojan horse and spyware.
Like a biological virus they can spread quickly and widely causing damage to the core functionality of systems corrupting files and locking users out. These types of programs can self-replicate and can spread copies of themselves which might even be. Worms are pieces of malicious code making copies of itself.
Thus malware includes computer viruses worms Trojan horses and also Spyware programming that gathers information about a computer user without permission. 7 Examples of Malicious Code 1 Computer Viruses. Malicious Code Software programs having malicious intent which are designed to infiltrate and damage computers without the users are.
Worms A worm is a malicious software which similar to that of a computer virus is a self-replicating program however in the case of worms it automatically executes itself. Differences between viruses and other malicious codes. Discuss and explain the various types of malicious code and how they work from BUSIENSS E-COMMERCE at University of Jordan.
Discussion Discussion 91 - Malicious Code Attack In order to understand threats and to develop practical and effective countermeasures you must understand the objective of malicious code attacks as well as what attackers are targeting. Industry studies have revealed that detection of malicious code often takes weeks or. Visiting infected websites or clicking on a bad email link or attachment are major gateways for malicious code to sneak its way into your system.
Up to 20 cash back Scripts worms and viruses can harm your computer by finding entry points that lead to your precious data. Next explain both the potential threat posed by viruses and other malicious codes. There are different types of cyber crimes that use malicious code to modify data and gain unauthorized access.
From the first e-Activity explain the key differences between viruses and other malicious codes. Next explain both the potential threat posed by viruses and other malicious codes and their main effects on computers and productivityDiscuss the fundamental lessons that we can learn. Identify the type of malware based upon the definition.
Mobile Malicious Code - web documents often have server-supplied code associated with. Malicious code includes a variety of threats such. Attacks may be launched through various means including viruses worms bots ransomware and Trojan horses.
The different types of malicious attacks are as follows. Two of the most common types of malware are viruses and worms. What are the Categories of Cyber Crime.
Reveton and CryptoLocker are types of malware known by what general term. Each type of malicious code attack can wreak havoc on a defenseless IT infrastructure very quickly or wait on servers for a predetermined amount of time or a trigger to activate the attack. Identify at least three 3 different types of viruses and describe the main differences between each one.
The different types of Computer virus are Memory-Resident Virus Program File Virus Boot Sector Virus Stealth Virus Macro Virus and Email Virus.
10 Types Of Malware How To Prevent Malware From The Start Norton

Malicious Code Malware Information Security Lesson 4 Of 12 Youtube
0 Comments